Security researchers warn against downloading Flash Player from the flash[.]cn site, because the version that is still distributed via the site in China after the EOL has now turned into adware, opening browsers at timed intervals and displaying ads and popups.
Security company Minerva Labs noticed that its products, which are apparently installed on many Chinese systems, were receiving corresponding security warnings related to this Chinese Flash Player version via telemetry. Upon subsequent analysis, the researchers found that while the app installed a valid version of Flash, it also downloaded and executed additional payloads. The compromised version downloaded and executed the nt.dll file.
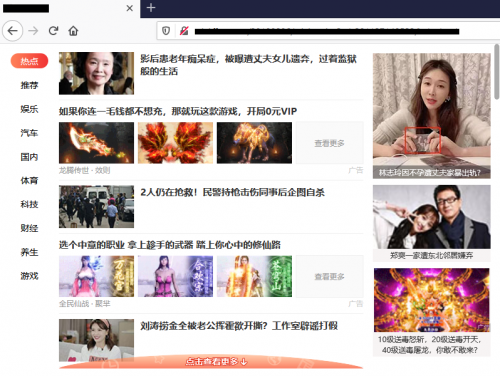
This file was loaded inside the FlashHelperService.exe process and periodically opened a new browser window displaying various ad-heavy and pop-up websites. The case once again shows how risky it is to download software from an unofficial site (where even manufacturer sites deliver infected software in supply chain attacks).
IOCs: Hashes: 8cb8e8c9fafa230ecf2f9513117f7679409e6fd5a94de383a8bc49fb9cdd1ba4 (FlashHelperService.exe) d51100ae4f9e972b5582a129c6756df494be3d18a6824d2ca125158a8ac29f2a (ServiceMemTask.dll) 9b9e8e6ae50774d27472c63d64bc7daeeac8bea05b6b3c3025fbaae12366e214 (tt.dll) 0916BA911B2B5FABAFE02EC5E5032CBA548B01E7F081CC20E3D28A6634FB56CB (nt.dll)
https://blog.minerva-labs.com/the-curious-case-of-flashhelperservice-0
https://borncity.com/win/2021/02/24/flash-player-fr-china-mit-malware-verseucht/
@火绒工程师
|